What are some common cyberattacks on nonprofits?
Malware

Malware is malicious software that infects, provides attackers remote control access to your devices, and steals your network’s data. While the most talked-about type of malware is ransomware, there are other types:
Spyware – It’s a type of malware that collects information about the user and communicates it to the cybercriminal.
Trojans – These are malicious software disguised as legitimate ones. Inadvertent users end up falling victim to these attacks when they download software and applications from unverified sources. Remember to always verify the provider and run a malware scan when you download an app.
Malvertising – These are malware combined with advertisements. When the user clicks on an infected ad, the malware automatically spreads into the device and the network.
Man in the middle attack
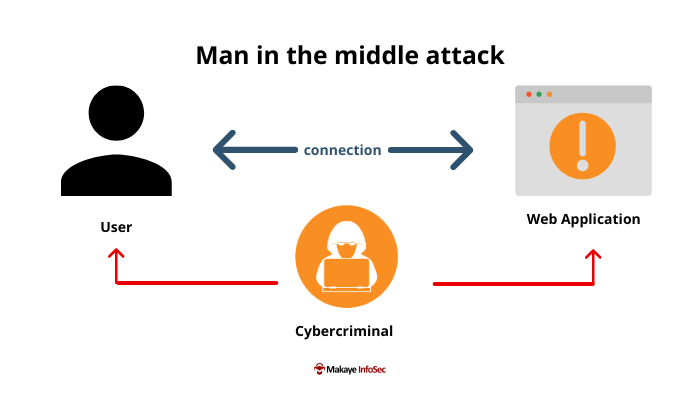
A man in the middle (MITM) attack occurs when an ill-intended user positions themselves between a user and an application with the purpose of stealing personal information such as credentials and financial data.
Denial-of-Service attack

A denial-of-service (DoS) attack occurs when an ill-intended user interrupts a device or system’s normal functioning. This type of cyberattack overwhelms a target device with an unusual amount of traffic, making the server slows down and eventually stop working, resulting in a denial of service to other users. For nonprofits, the immediate effects are a lack of access to records and files, making operations impossible.
Is your nonprofit at risk? Take a look at these resources that might help you step up your cybersecurity game:
Learn how this guide to cybersecurity for nonprofits can support your mission and operations.
This cybersecurity checklist will help you understand if your nonprofit is at risk. Use them as a starting point in your next cybersecurity meeting.
This whitepaper will help you understand what are the main differences between IT and InfoSec professionals.
Understand if your nonprofit is at risk. The knowledge gained through this assessment will help guide the decisions that will need to be made to improve your security and align your risk with acceptable tolerance levels.